
When looking for suppliers, companies want to make sure they’re making the right decisions that are not putting their own businesses in jeopardy. If you’re selling your products or services to other companies, especially larger organizations, you might’ve encountered terminology like SOC 2 reports, SOC 2 compliance, security audits, etc. In this article, we’re going to provide you with an understanding of what SOC 2 compliance means, why your prospect might’ve asked about it, and who can benefit from achieving it.
What is SOC 2?
SOC 2 stands for Service Organization Control Type 2 and is a Cybersecurity Compliance Framework. It’s defined and developed by the AICPA (American Institute of Certified Public Accountants). The purpose of this framework is to certify the correct use, storage, and handling of data by an organization.
An organization that goes through a SOC 2 audit process ends up with a report stating how they meet set expectations in regards to how they handle data within their control. In contrast to traditional certifications, where everyone is compared to the same reference bar, SOC 2 requirements vary significantly from company to company. When approaching an SOC 2 audit, a company has to define its own security controls based on the SOC 2 principles.
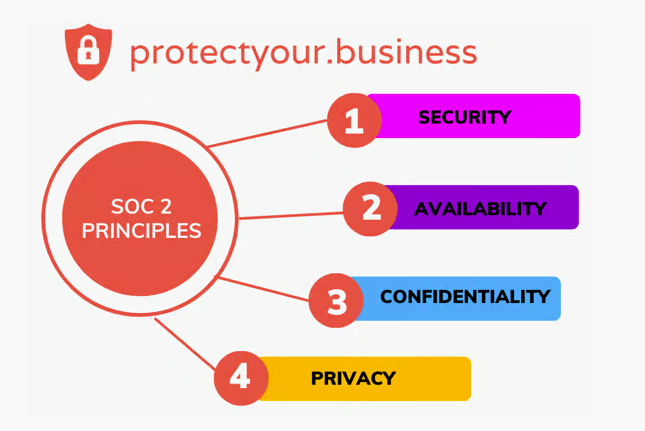
What are the SOC 2 Principles?
The following principles are areas in which companies define their security controls that are then audited and documented in the SOC 2 report.
- Security: Protection of data and systems
- Availability: Rate to which Service Level Agreements (SLA) are met
- Confidentiality: How a company is able to restrict access of sensitive information to the intended group of people and systems
- Privacy: The company’s compliance with their own data usage principles and applicable national and international regulations.
What is a Security Control?
A Security Control is a documented policy, process, or procedure that defines how the organization aims to adhere to the SOC 2 principles and can be tested and verified by an independent auditor.
- Password management: This includes controls that ensure that passwords are strong and that they are not shared with unauthorized individuals.
- Physical access control: This includes controls that restrict who has physical access to sensitive data and facilities.
- Data backup and recovery: This includes controls that ensure that sensitive data can be restored in the event of a data breach or other incident.
- Vulnerability scanning: This includes controls that identify and remediate security vulnerabilities in an organization’s systems and applications.
The requirements for these protection mechanisms are specific to the business a company conducts and the level of maturity it has. Over time, controls become more stringent and cover more aspects of an evolving business.
These controls are then tested to determine to what extent they are met. These results are then documented in the SOC 2 Report, which is often shared with prospects or customers that require their suppliers to be SOC 2 compliant.
Do I need to be compliant with SOC 2 Compliance?
This article is assumed to be mostly read by leaders of Small & Medium Businesses, including Tech-Startups. For smaller organizations it can be a daunting task to start and maintain an SOC 2 program, just because a potential customer asks for it.
To answer the question of the necessity of being SOC 2 compliant, you have to understand how much of a requirement it is for the type of customers you’re trying to sell to.
Put yourself in the shoes of your prospect. When deciding on a supplier for a given service, they often have implicit or explicit requirements that are used to compare various options and achieve a fair decision. If you’re selling to customers that generally require SOC 2 compliance, not having it might not be a deal-breaker in itself, but it often puts you at a disadvantage.
Ask yourself: How much of your yearly revenue do you plan to make with organizations that have these requirements? How many of the deals you lost actually needed SOC 2 compliance?
Especially early-stage founders often get nervous when that one large prospect they could only dream about winning asks about SOC 2. As a general rule of thumb, if a customer seems unreachable, SOC 2 compliance is unlikely to make a difference. If the market generally asks for it, you should consider getting it.
I hope that this was a useful read. Please feel free to reach out for an informal discussion on how we can help you with this and other types of security questions.
- How to Identify Insider Threats? - June 13, 2024
- How to Detect and Remove Malware from Android Devices: Protecting Your Ecommerce Business - June 8, 2024
- Protecting Your E-commerce Business from Malware Threats - June 7, 2024



