
Cybersecurity risk assessment is crucial in running a small business because it involves taking risks to achieve desired success. These risks include investing in marketing, hiring employees, purchasing tools for providing services, and more.
In today’s digital age, a significant part of running a business relies on the internet, digital services, and devices. Embracing an online presence offers numerous opportunities for businesses to enhance efficiency, surpass traditional limitations, and maintain closer customer interactions.
However, it also exposes businesses to new types of risks that were not encountered by traditional brick-and-mortar shops. As each company utilizes its IT tools differently, the risks associated with always being connected are highly individualized. This is where the value of a cybersecurity risk assessment becomes evident.
What is a Cybersecurity Risk Assessment?
Certainly! Here’s the cleaned-up version of the text:
Conducting a Cybersecurity risk assessment involves examining how the use of technology and related processes can negatively impact the viability of your business. The complexity and cost of such an assessment can vary widely
Certain compliance frameworks, such as SOC 2, ISO 27001, and HIPAA, are established and either required or highly recommended for companies operating in spaces where system security is crucial.
Cybersecurity risk assessment can also be carried out on a smaller scale if a company wants to focus on specific risks and their mitigation.
Regardless of the scope, a security risk assessment is performed by a security assessor following a pre-defined protocol of questions and checks to identify pressing risks that could adversely affect the company.
The step-by-step Cybersecurity risk assessment approach typically involves:
- Understanding the systems and technology used and their contribution to the company’s success.
- Understanding the defined processes for interacting with these systems and managing changes.
- Understanding the policies that employees and contractors must follow, ranging from data usage to HR policies.
- Identifying how potential misuse by internal and external factors could negatively impact the business.
- Ranking the identified risks to prioritize those that require immediate attention.
Compliance frameworks help define the required level of security and where improvements are mandatory. Even without such frameworks, a Security Risk Assessment remains a valuable tool for business leaders to comprehend potential pitfalls and acceptable risks within the broader context of the company.
It’s important to remember that a Security Risk Assessment is a snapshot of the security state at a specific point in time. It does not replace the need for sensible, ongoing processes when using IT tools in the business.
Who needs a Security Risk Assessment?
Traditionally, Security Risk Assessments were mainly conducted by companies operating in regulated industries like finance, health, or publicly traded sectors. However, with the decreasing cost of deploying IT tools to enhance business reach and efficiency, the number of small businesses considering themselves predominantly online-operated has increased. Consequently, more companies now heavily depend on the availability and integrity of their digital assets for success.
In today’s landscape, any company relying on its IT infrastructure to deliver reliable and accessible services to customers can benefit from conducting some level of Security Risk Assessment. The outcomes of such an assessment can provide valuable insights to the business regarding necessary investments to strengthen security measures.
Isn’t my Business too small for a Security Risk Assessment?

Even if your business doesn’t operate custom-built technology or proprietary systems to serve customers, you might think that conducting a Security Risk Assessment is excessive. However, even a simple audit of basic processes, such as employee onboarding and offboarding or customer data storage, can offer valuable insights. These insights can help identify process improvements that will effectively reduce cyber-related risks.
What’s in scope for a Security Risk Assessment?
Certainly! Here’s the cleaned-up version of the text:
The answer is quite comprehensive – “everything.” A Security Risk Assessment covers the devices you use for work, the installed software, the way you utilize these tools, the protection of private data, and much more. Below are several areas that can be included in such an assessment:
Infrastructure:
- Electricity and power redundancy
- Network equipment and Firewalls
- Fire suppression systems
- Security Cameras
- Physical access controls
Hardware:
- Computer and mobile devices
- Data Storage devices
- Sensors and Printers
Software:
- Software versions
- Vulnerability reports
- Update policies
Processes & Policies:
- HR Onboarding / Offboarding
- Access Control
- Data Storage policies
- Regulatory requirements
These are just a few examples of what can be considered within the scope of a Security Risk Assessment.
Even the smallest business handles some form of customer data, utilizes tools and processes to communicate with customers, and may need to comply with regulatory requirements such as GDPR in the EU. Therefore, conducting a Security Risk Assessment can benefit businesses of all sizes.
How can I get a Security Risk Assessment?
The initial step is to engage with someone who can assist you in defining the scope of the assessment that suits your specific requirements. At ProtectYour.Business, we prioritize understanding the unique needs and level of readiness of our customers. We identify areas that require close attention and those that can be assessed at a later stage or, if necessary, omitted.
Our approach to working with partners and customers is consistently structured, following these steps:
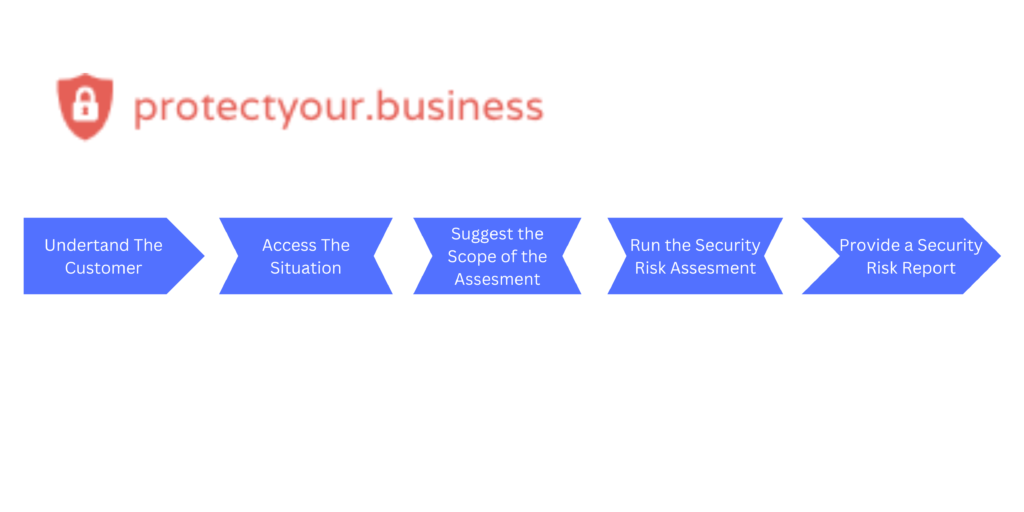
By tailoring the assessment to your specific needs and gradually addressing the identified areas, we aim to provide a comprehensive and pragmatic security evaluation for your business.
If you have any questions in regards to your Business Security risks, please contact us for an informal, free consultation.
- How to Identify Insider Threats? - June 13, 2024
- How to Detect and Remove Malware from Android Devices: Protecting Your Ecommerce Business - June 8, 2024
- Protecting Your E-commerce Business from Malware Threats - June 7, 2024



